
September 6, 2023 • 16 min read
NIST Cybersecurity Framework (CSF) Controls Fundamentals

Kelley Spakowski
50% of companies use NIST CSF because it offers a single framework that offers a comprehensive process and prescriptive maturity levels for multiple cybersecurity needs. The National Institute of Standards and Technology, often referred to as NIST, was founded in 1901. Now a part of the US Department of Commerce, NIST supports technology, commerce, and manufacturing with its research, measurements, and standards. Driven by an Executive Order in 2013 focused on “Improving Critical Infrastructure Cybersecurity,” NIST released the first version of its cybersecurity framework (CSF) in 2014. The NIST CSF would be revised in 2018 — as of 2023, NIST has solicited comments for CSF 2.0. Many organizations now leverage the NIST CSF and its control guidance as a baseline for their information security programs and for safeguarding sensitive information. NIST works with federal agencies to develop best practices in accordance with FISMA.
Despite its popularity, the NIST CSF is intimidating at first glance. Where should organizations start with the framework? How can security controls feed into and supplement risk management activities that are taking place, like risk assessments? What are the enhancements that companies should implement for improved data security and system and information integrity? Where does the NIST CSF fit among other security standards, like ISO 27001? Is compliance with the CSF a regulatory requirement? We’ll cover all that and more!
What is the NIST Cybersecurity Framework (CSF)?
The NIST CSF is a set of “standards, guidelines, and practices to promote the protection of critical infrastructure.” Though driven by the federal government to address national security threats and protect federal information systems, the CSF is flexible enough to be adopted by organizations in any sector and of any size. The CSF outlines five functions critical to security programs, with each function containing 23 unique categories. Each category is further broken down into subcategories that describe specific objectives for developing and implementing a robust information security program and protecting critical information systems. There is considerable overlap between NIST controls and other information technology security controls, and NIST guidance can often be used to meet compliance requirements associated with other cybersecurity frameworks or standards.

The CSF has been supplemented by additional, more prescriptive guidance through NIST SPs or “Special Publications.” NIST 800-53 in particular provides implementation guidance for security and risk across 20 control families that should look somewhat familiar to anyone who’s worked on IT general controls (ITGCs), other regulatory programs like HIPAA, or with other information system security frameworks. NIST SP800-53B contains the control baselines organizations can use to tailor their approach to applying security controls for each system, based on that system’s criticality to the business.
We’re only discussing the NIST Cybersecurity Framework in this article, but NIST issues guidance for a variety of sectors and industries. They have also released a Risk Management Framework (RMF) that complements the NIST CSF, and helps organizations develop and enhance their risk management strategy.
What are NIST Control Families?
The NIST Cybersecurity Framework has 20 distinct control families, outlined in NIST SP 800-53, which consist of base controls and control enhancements. Base controls are the fundamental controls that need to be implemented to meet that particular objective or address a certain risk. Control enhancements are applied to base controls to augment them and offer additional security for especially sensitive data or systems. NIST also emphasizes the importance of policies and procedures that document an organization’s approach to managing cybersecurity risk and addressing each area of the NIST control families in some capacity.
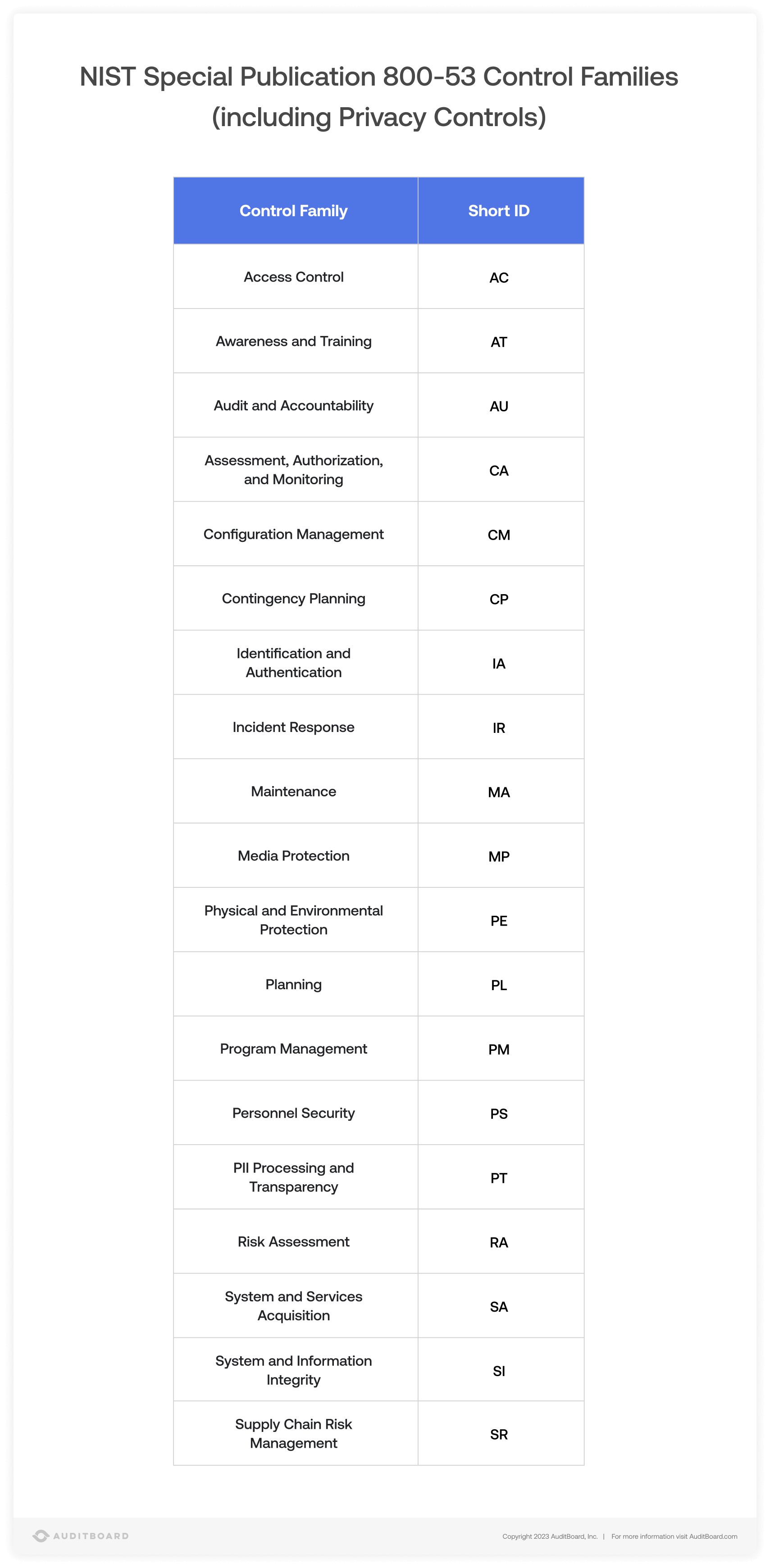
We’ve highlighted a few key control families and expanded upon them further: Access Control; Program Management; and Supply Chain Risk Management.
Access Control
Access controls are a critical area of security and risk management even beyond the arena of cybersecurity. Improper access controls can result in unauthorized or inappropriate access to sensitive information, and carries the risk of data leakage and data exposure. Access controls dictate everything from how accounts are created and managed; to who gets access to what facilities and data; to overseeing remote access mechanisms and security. Following the principle of least privilege – and limiting user access only to those functions they need to fulfill their role – form the basis of access control best practices.
Program Management
Program management doesn’t always have an analogue in other cybersecurity frameworks. It combines the definition of roles in information security and the overall plan for information security at the organization with risk management and privacy planning. The intent of this control family is to document and communicate the organization’s high-level, overarching approach to information security and privacy. The concept of an ISMS is similar to the program management family.
Supply Chain Risk Management (SCRM)
Supply chain risk management, also known as vendor or third party risk management, involves assessing and addressing the risks associated with the organization’s supply chain and third party providers. Considerable risk, especially in the cybersecurity space, can now originate or pass through the supply chain, rendering organizations vulnerable through another attack vector. With increased scrutiny on supply chain security, organizations that rely heavily on their third party suppliers should pay increased attention to this area of risk management.
What are the Differences Between NIST and ISO?
There are a few fundamental differences between the NIST CSF and ISO’s corresponding information security management system (ISMS) standard, ISO 27001, though they both seek to address cybersecurity risk and provide guidance to organizations for protecting information systems and sensitive data.
Three differences between the NIST CSF and ISO 27001 involve certification, maturity scales, and cost.
Certification
One core difference between the NIST CSF and ISO 27001 is the availability of a certification. While both are voluntary standards — that is, they’re not required for any organization to adopt, ISO 27001 provides companies with the opportunity to undergo a third party audit in order to achieve certification under the standard. This can have benefits for service providers seeking to build trust and demonstrate strong security practices to customers, partners, and other stakeholders. ISO 27001 is especially relevant to companies doing business in the EU and internationally. On the other hand, while there is no “NIST certification,” organizations can seek compliance with NIST and undergo security assessments that can measure adherence to NIST CSF guidance and recommendations.
Maturity Scale
Another difference separating NIST’s CSF and ISO 27001 is related to the question of compliance and certification in that NIST does not offer a certification or attestation, but rather invites organizations to rate their cybersecurity maturity on a scale of one to four, known as a “Framework Implementation Tier.” Meanwhile, with ISO 27001 and particularly in regard to certification audits, there are two outcomes of compliance or noncompliance, and no maturity scale.

Cost
While it’s not entirely accurate to say that implementing the NIST CSF does not have a cost — there are certainly resources and effort that must be expended to implement the framework’s security controls and methodology — the actual guidance is available at NIST’s website for free. And, since there is no certification associated with the NIST CSF, there’s no requirement to involve a third party auditor. ISO 27001’s guidance is not free, though reasonable, but achieving certification comes at a greater cost. ISO 27001 certification requires an initial audit, then two subsequent years of surveillance audits, then another certification audit, all requiring the services of a third party auditor and accompanied by those costs.
Functions of the NIST Framework
In conjunction with the 20 control families found in NIST Special Publication 800-53, the NIST CSF defines five core functions that together address cybersecurity risks. The five functions of the NIST CSF are: Identify, Protect, Detect, Respond, and Recover. These functions are further broken down into 23 Categories. NIST emphasizes that these functions must work in tandem and continuously to achieve optimal results and combat the dynamic threat landscape.
NIST also asks companies to consider their target tier of implementation or maturity (levels one through four), and where they might be in the present day. As part of that assessment, the business should consider their overall “profile,” or the unique combination of business objectives, threats, and regulatory and compliance requirements and controls that make up the company.
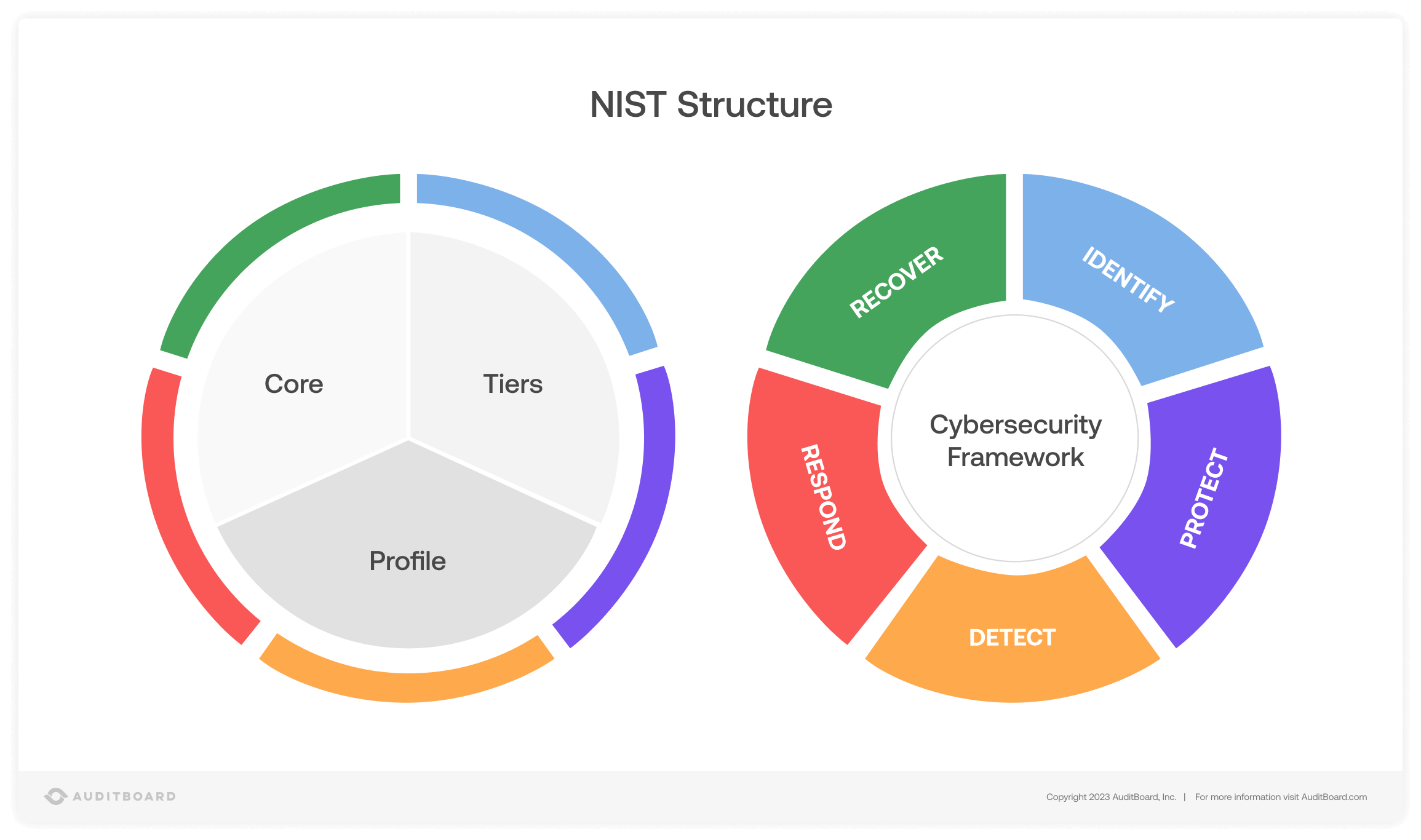
Identify
The identify function of NIST includes the categories of Asset Management, Business Environment, Governance, Risk Assessment, and Risk Management Strategy. This component of the framework asks organizations to understand and inventory available assets and the business context in order to prioritize initiatives and better meet the company’s needs and objectives. Identifying in the context of the CSF also involves discovering risks through risk and security assessments. This core function gives the business a macro and micro view of the organization’s cybersecurity risk exposure and security posture.
Protect
The protect function of the NIST CSF involves creating and implementing controls and processes that safeguard sensitive information and key systems while also mitigating risks. Categories in this function are: Identity Management and Access Control; Awareness and Training; Data Security; Information Protection Processes and Procedures; Protective Technology, and Maintenance. These activities take place at every level of the organization, with access controls affecting every person in the company, and security awareness training incorporated as a security requirement. The protect component of the NIST CSF also includes establishing security policies and procedures that focus on limiting the impact of a potential security incident.
Detect
Detecting in the NIST CSF involves discovering cybersecurity events in time, and implementing continuous monitoring capabilities and processes to support this function. This component of NIST includes Anomalies and Events; Security Continuous Monitoring; and Detection Processes. Detection includes the potential for insider threats to cause a cybersecurity event; thus a good detect function would take into account internal activity and consider the potential risk associated with a disgruntled employee or other internal risk factor. Timeliness is a key factor in this component of the CSF, and the closer to real-time detection your organization can get, the more prepared it will be to respond to and remediate issues.
Respond
The respond function in the NIST CSF includes Response Planning, Communications, Analysis, Mitigation, and Improvements — that is, how to take action and handle a cybersecurity incidentfrom start to post-mortem. This function ensures that all necessary personnel and levels of the organization have documented plans and are equipped to address security incidents that affect the company. The respond function of NIST even incorporates a category on communicating about incidents, both internally and externally.
Recover
Recover in the NIST CSF includes Recovery Planning, Improvements, and Communications, and covers the resilience and restoration capabilities of an organization after a cybersecurity event. Getting back to normal operations is a crucial part of addressing cybersecurity incidents, and putting frequent backup controls and a clear contingency plan in place can streamline that process considerably. A mature recovery process would consider the order of operations for system recovery and restoration, as well as recovery metrics and objectives.
Tools for Compliance with the NIST CSF
Complying with the NIST CSF and striving to evolve your organization’s cybersecurity posture and maturity levels will transform any information security program and bring it to the next level, providing leadership, stakeholders, customers, and the public with greater assurance that your company is following security best practices and cares about protecting sensitive information. The CSF gives deep guidance on how to implement and enhance controls, and plays well with other compliance and regulatory frameworks — but that also makes implementation of the NIST CSF a little complicated. How do you keep track of all your control mappings, risk assessments, and mitigation plans? How can you get the right people “in the room” to address incidents?
Purpose-built risk management software, vetted and used by actual risk and audit professionals can make your NIST CSF journey a breeze. With built-in collaboration tools to wrangle your stakeholders, view mappings of controls and frameworks, and upload evidence to a central repository, AuditBoard can help your business mature its cybersecurity program.
About the authors

Kelley Spakowski is an IT Risk and Compliance Specialist at AuditBoard. Kelley is the former creator and host of the GRC & Me Podcast, and an experienced GRC software and services solutions professional. Connect with Kelley on LinkedIn.
You may also like to read

What is the Colorado AI Act? A detailed guide to SB 205

What is the EU AI Act?

What is the NIST AI Risk Management Framework?
Discover why industry leaders choose AuditBoard
SCHEDULE A DEMO



