
September 14, 2023 • 22 min read
Vendor Risk Management (VRM) Fundamentals

Syed Khan
The importance of robust vendor risk management, or “VRM”, practices has been illustrated by a number of cyberattacks and data breaches that have originated from vendors and gone on to significantly impact the organizations using their services. The recent MOVEit attacks were able to impact well-known brands like the BBC, British Airways, and even the Big Four accounting firms. The breach of Kaseya, a Managed Service Provider (MSP) offering remote IT operations solutions and management, had a downstream impact on the customers using their technology and services. That said, vendor risk management as a practice and a concept is not new — many organizations have established vendor, supplier, or third-party risk management (TPRM) functions integrated into their GRC programs. However, in today’s dynamic cybersecurity risk landscape, an updated approach to VRM is needed to safeguard companies and their customers.
Vendor risk management encompasses all the processes and systems involved with managing vendor risk, from vendor selection and due diligence, through procurement and onboarding, to ongoing monitoring and ultimately offboarding, should that be necessary. An effective vendor risk management process allows companies to identify risks associated with third-party vendors, understand the impact of third-parties on the organization, meet compliance and regulatory requirements like GDPR and HIPAA that require VRM controls, and foster mutually beneficial vendor relationships. Furthermore, a good VRM program can play a major role in an organization’s information security posture and enable stakeholders to make informed choices about third-party relationships.
Vendor risk management is also known as third-party risk management, supply chain risk management, or supplier risk management. In this article, we will use these terms interchangeably, but know that some regard “supplier” and “supply chain” as only pertaining to physical products or services.
What is Vendor Risk?
Vendor or third-party risk is any risk that originates from relationships with vendors and third-parties. There are many different types of vendor risk that could have varying levels of impact on an organization, should those risks be realized. With companies growing more and more intertwined and interconnected, vulnerabilities that open up pathways between different companies can be exploited, and so the reach of a successful third-party or even fourth-party attack could be expansive. Managing the risk exposures that come with partnering or doing business with a third party, whether they play a large role in your organization or a negligible one, is why the practice of vendor risk management exists.
What Types of Vendor Risk are There?
Many types of vendor risk should be familiar to any students of risk management. They fall into categories that have already been defined, like operational risk, regulatory and compliance risk, reputational risk, strategic risk, financial risk, cybersecurity risk, ESG risk, business continuity risk, and geopolitical risk.
Operational Risk
Operational risks are any occurrences that could cause a disruption to day-to-day operations and business processes, resulting in losses of some kind. Operational risks encompass employee conduct and errors and system failures. A company that relies on a third-party for company communications might have an operational risk associated with using that vendor, should an outage occur or services get suspended. If that were to occur, the company would suffer a loss of productivity due to members of the workforce being unable to communicate.
Regulatory and Compliance Risk
Regulatory and compliance risk stems from the consequences of failing to adhere to requirements or comply with standards. Those consequences can range from fines to losing business relationships, among other potential outcomes. Vendor relationships can cause this risk to be realized when and if a vendor fails to implement or execute controls that are part of your contractual agreement with them. As an example, if a vendor fails to conduct an access control that your organization needs completed in order to comply with a certain framework, that could jeopardize your compliance posture.
Reputational Risk
Vendor relationships can lead to various flavors of reputational risk. Sometimes, even doing business with a certain company can negatively affect the reputation of your organization. Ethical missteps made by a third-party can come back to haunt their customers and partners.
Strategic Risk
Strategic risks are those potential risks that could affect a company’s tactics, strategy, and objectives. These risks can be realized when a third-party’s actions, values, and behaviors are incompatible with your organization’s. A circumstance like a third-party ceasing to support an application that your company relies on, or that chooses to terminate its relationship with your company, could pose a risk to strategy.
Financial Risk
Financial risks associated with vendors can be anything that causes the business to lose revenue, pay excessive costs, or otherwise affect their financials. Fraud can play a role here as well, if bad actors are able to gain access to your company’s assets through a vendor.
Cybersecurity and Information Security Risk
Perhaps the most headline-generating risk area right now, cybersecurity and information security risks, are related to the protection of the organization’s sensitive information, IT assets, and systems. Vendors signify an area of vulnerability for many companies, especially as they invite third-parties into their IT environment and share confidential or sensitive information in the course of doing business. Third parties that do not have robust security controls, or that suffer a cyberattack of their own, may provide cyber criminals with a pathway to compromise the clients and customers of that vendor. The mitigation of cyber risks that stem from third-parties is a critical objective of a third-party risk management program.
ESG Risks
ESG risks, or Environmental, Social, and Governance risks, can be realized when vendors act in opposition to a company’s stance and objectives related to ESG. Vendors that cause environmental damage, carry out labor and human rights violations, or that are corrupt, threaten an organization’s position on ESG matters, and should factor into that third-party’s vendor risk assessment.
Business Continuity Risks
Business continuity risks materialize when a third-party is unprepared for disaster scenarios or threats to their going-concern. Their cessation of operation can have a large impact on your organization’s operations.
Geopolitical Risks
Geopolitical risks can be realized if your vendor is located in an area, country, or region that is experiencing unrest, corruption, or human rights violations. Due to geopolitical conditions, a vendor may be unable to continue providing products or services, potentially affecting your organization.
Why Vendor Risk Management is Essential
Implementing and maintaining a thorough and robust VRM program is essential for modern businesses as they incorporate more third-party services into daily operations, and even start businesses on the platforms of third-party vendors. The public clouds maintained by Amazon (AWS), Microsoft (Azure), and Google (GCP) are one example of how embedded third-party products and services are in the business world. As companies put more trust in third-parties, the role of third-party risk management in vetting and evaluating potential vendors becomes more and more important. Vendor risk management programs and processes give organizations a way to onboard service providers with confidence, maintain data security and protection, protect their reputation, and meet compliance and regulatory requirements.
Onboard Service Providers and Vendors with Confidence
With a high-quality vendor risk management program, companies can be sure that they are procuring and partnering with reputable, reliable providers. VRM programs look to understand and evaluate suppliers before they make it into the organization’s environment, empowering stakeholders to make informed procurement decisions about the vendors they choose to work with. By performing due diligence on third-parties during vendor selection, companies can gain assurance and confidence that their vendor relationships will be productive and meet business needs.
Data Security and Protection
As VRM teams partner with procurement stakeholders to assess potential vendors, they take into account the need to protect sensitive data and information. Effective VRM processes incorporate data security requirements into their vendor selection criteria so that vendors can’t get into the ground floor without having security controls in place. With the cost of data breaches skyrocketing, companies can’t afford to entrust their information and data with untrustworthy or unreliable vendors.
Compliance and Regulation
In addition to data security requirements, third-party risk management teams should integrate compliance and regulatory requirements into their assessment of potential third-party vendors. Having a third-party that is willing and able to comply with necessary standards, like GDPR, HIPAA, and PCI is invaluable, and can save your company a lot of headache during an audit or assessment. It’s helpful to make lists of mandatory controls that vendors must have in place to meet your organization’s obligations and mandates.
Benefits of Effective Vendor Risk Management
Effective vendor risk management isn’t just essential — it’s beneficial for your business. Outsourcing functions allows a company to streamline its operations and only focus on those areas that they have a competitive advantage in. Having vendors take care of back office and non-critical processes enables organizations to focus on their core value proposition.
Beyond the efficiencies that can be gained by working with third parties, TPRM or VRM are typically mandatory for most compliance frameworks and standards. By not having a vendor risk management program established, your organization may be putting their compliance objectives at risk.
Finally, an effective vendor risk management program does involve building positive and productive relationships with stakeholders both internally and externally. When vendor relationships are positive, there are more opportunities to form partnerships and learn from one another. Vendors may develop new solutions or products that fulfill needs or solve problems at your company, or come up with creative solutions for shared corporate challenges.
Building a Vendor Risk Management Program
Building a vendor risk management program takes a few steps, but the actual vendor risk management process is very repeatable, and vendor management follows a regular lifecycle.
A vendor risk management program usually starts at the vendor selection step, in which a company is looking to procure a service, product, or solution from a third-party to solve a problem that they have. Then, after completing due diligence and comparing vendors, selection will occur. From there, the company’s VRM function will perform an initial vendor risk assessment, then continuously monitor vendor performance. Any risks will be identified, analyzed, and treated, and vendors will follow a re-assessment schedule based on their risk score.
Effective Vendor Selection
Effective vendor selection is both the objective and the cornerstone of successful TPRM programs. The procurement team, relevant stakeholders, and the vendor risk management team would partner to determine a set of criteria that new vendors would have to meet in order to be considered by the company, including requirements around cybersecurity, business continuity, availability, and general internal controls. These vendor selection steps may already be documented and have corresponding templates at your organization — if not, it’s wise to turn them into templates.
From there, the procurement team and relevant stakeholders would select a small subset of vendors that meet the preliminary criteria, and evaluate each in depth. This phase might involve scheduling demos, speaking to customers and sales representatives, performing trials, and refining the vendor selection criteria. Over time, the number of eligible vendors will narrow, leading to the due diligence process.
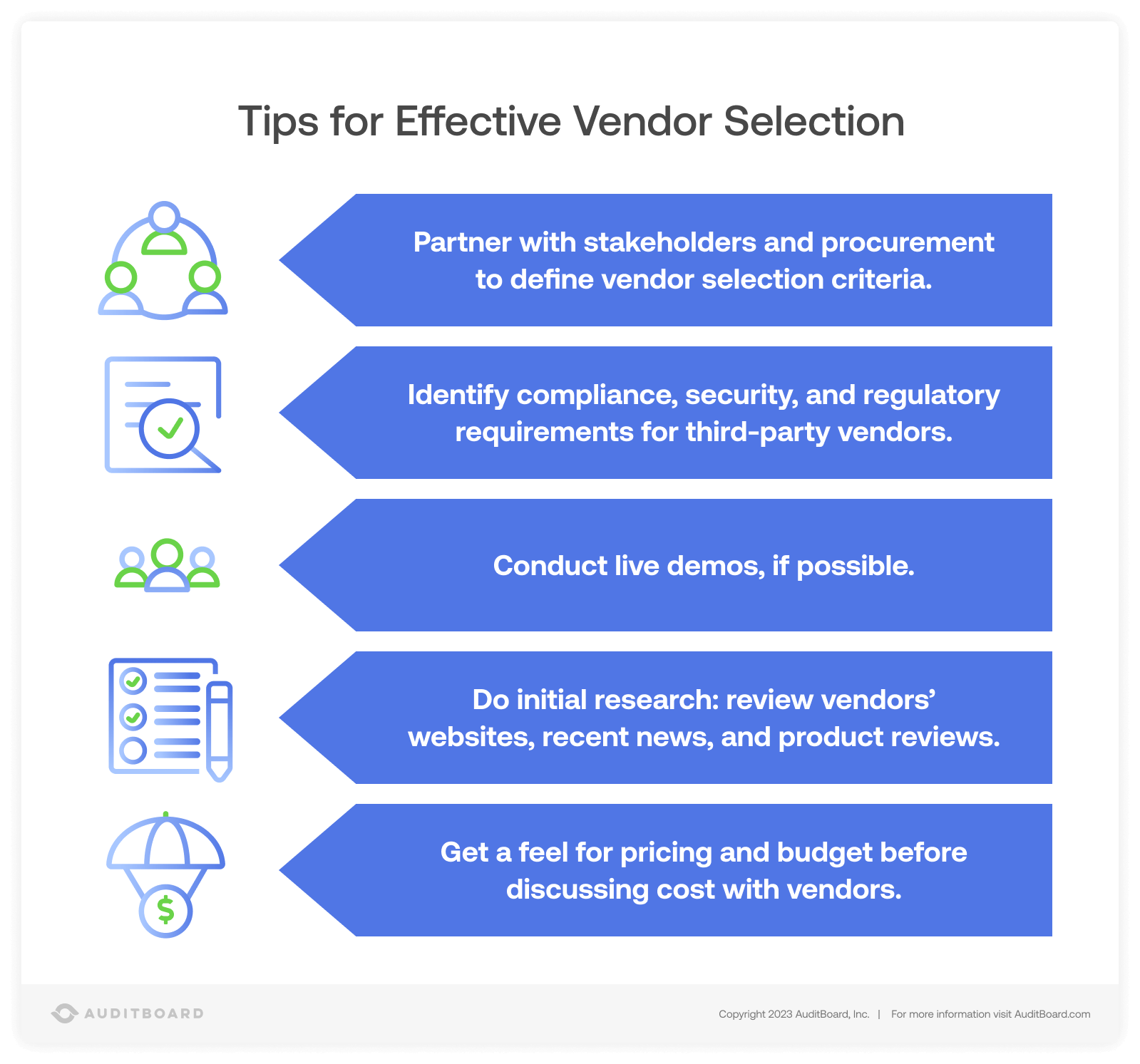
Due Diligence
As vendors become candidates for selection, they are usually subject to a due diligence process that may involve responding to a questionnaire or furnishing evidence of sound company and security practices. Certifications like ISO 27001 or attestations like SOC can make the due diligence process easier for service providers, as they indicate that a company has taken steps to adhere to a risk management and/or cybersecurity framework, and often demonstrate a strong security controls environment. Collaborating with stakeholders and procurement, the VRM team will collect all the required due diligence materials and documentation, and review it, forming an evaluation of scoped-in vendors. Completing due diligence ensures that the selected vendor will be able to meet the company’s requirements in terms of controls, regulatory requirements, services, and other key parameters for sealing the deal. Ultimately, it will be up to the stakeholders, procurement, and management to make a final selection on the vendor.
Vendor Risk Assessment
Once a vendor is selected and as they are being onboarded, the vendor risk management function should conduct a vendor risk assessment and enter the new vendor into the organization’s “vendor” or “third-party” inventory. This inventory is a list of all the third-parties the company is contracting with, accompanied by a description and a risk score. Beyond those fields, it is up to the organization how they would like to structure their vendor inventory.
Completing a vendor risk assessment, at its core, involves understanding the vendor, what they are providing to the company, and what role they will play. A vendor’s risk tier is dependent on how reliant the organization is on that vendor’s product(s) or service(s). If your entire business is built on AWS and they were to suffer a widespread outage, your business would suffer an outage as well. In that scenario, AWS would be a high-risk vendor. On the flip side, if your company provided Spotify to all of your employees as a default service, or perhaps an organizational perk, and Spotify experienced an outage, there would be very little or no impact on your company. Thus, Spotify would be categorized as a low-risk vendor. High-risk third-parties require a more frequent refresh of their vendor risk assessments, ideally annually; while low-risk third-parties will be fine if they are only reviewed every three years. These intervals can be defined by the company in its TPRM policies, though high-risk vendors should be reviewed each year at minimum.
A company’s vendor inventory, as a whole, should be reviewed each year as well.
Continuous Monitoring and Performance Monitoring
As with any risk management function, companies should perform continuous monitoring over vendor performance to evaluate whether a given third-party is completing its obligations and adhering to the terms of your contract. There are many other alternatives to tools, products, and services available, and businesses should maintain a wide view of the third-party landscape. An existing vendor relationship may not be the best or most cost-effective choice.
Risk Response and Remediation
Throughout monitoring, VRM teams should remain vigilant for new risks, or changes to vendor risks and relationships that could impact the organization. Any identified risks should follow the risk management lifecycle and be documented before going through treatment and/or mitigation.
Conducting a Successful Vendor Risk Assessment
Executing a successful vendor risk assessment involves synthesizing various sources and forms of information in order to evaluate and form a conclusion about a third-party vendor’s risk level and security posture. As part of a good vendor risk assessment, companies should consider and understand:
- What was the driver for seeking out a new vendor product or service? – Understanding the challenges that the organization is facing, and the purpose for which a vendor is needed makes it easier to specify the parameters a vendor must meet and the risks that might result.
- How reliant will the organization be on this vendor? – This question helps determine a third-party vendor’s risk tier — the more reliant the company will be, the higher the risk associated with that third-party.
- What are the risks associated with using this product or service? – These will be risks captured in your risk register and treated as part of risk response.
- What controls, policies, and regulations does your organization need vendors to comply with? – Some third-parties may be unable or unwilling to meet your organization’s compliance needs, excluding them from selection.
As the team conducts the vendor risk assessment, they should capture their notes and conclusions in writing, ideally in a vendor risk management repository.
How AuditBoard Can Help You Mitigate Vendor Risk
AuditBoard’s vendor risk management software can help your organization level up its vendor risk management program by providing workflow automation capabilities, a central repository for working on and storing evidence and documents, plus dashboards and metrics that will tell you and your team more than spreadsheets ever could. You can simplify third-party vendor onboarding and streamline vendor assessments by using built-in logic and tools, while staying informed about vendor risks. Try AuditBoard today to raise your VRM program to the next level.
About the authors

Syed Khan, CPA, is a Manager of Implementation at AuditBoard, with a focus on the CrossComply module. Prior to joining AuditBoard, Syed spent several years in the audit, risk, and compliance space, and was most recently a Manager in the Risk Advisory and Compliance Services practice at Moore Colson CPAs and Advisors. Connect with Syed on LinkedIn.
You may also like to read


Shadow AI: Audit privacy risks in your data supply chain

IT vendor risk management: Best practices for managing third-party tech risk

The ultimate vendor risk assessment checklist for compliance teams

Shadow AI: Audit privacy risks in your data supply chain

IT vendor risk management: Best practices for managing third-party tech risk
Discover why industry leaders choose AuditBoard
SCHEDULE A DEMO



