April 19, 2024 • 20 min read
SOC 2 Compliance Checklist and Best Practices for an Audit

Tony Luciani
SOC 2 (System and Organization Controls 2) is a comprehensive auditing framework developed by the American Institute of CPAs (AICPA) to ensure that service providers securely manage data to protect the interests and privacy of their clients. There are various types of SOC (System and Organization Controls) reports for service organizations, including SOC 1 for internal control over financial reporting (ICFR) and SOC for Cybersecurity. However, one of the most widely sought-after information security attestations is the SOC 2 report. SOC 2 reports are intended to meet the needs of businesses requiring detailed information and assurance regarding their IT vendors’ controls relevant to the security, availability, and processing integrity of the systems used to process users’ data, and the confidentiality and privacy of the information processed by these systems. SOC 2s are versatile and revolve around the product, solution, or service that an organization is providing. SOC 2s have gained increased popularity among startups as an accessible, flexible compliance standard that improves internal practices, more efficient operations, and a better-defined organizational structure.
Benefits of a SOC 2 Report in Business
If your company provides technical solutions, the first step in earning the trust of customers is providing assurance over your scope with the AICPA’s Trust Services Criteria (TSCs) through a SOC 2 report. In particular, service organizations benefit from the following advantages of having a SOC 2 report:
- Peace of mind that your security controls are designed and operating effectively over a period of time (Type II).
- Ability to efficiently and effectively respond to IT, data security, and due diligence questionnaires from customers and/or partners.
- Ability to provide assurance to clients and partners that your business meets their standards, expectations, and their compliance requirements.
- Helps win more customers, boost sales, and gain an advantage over the competition by creating trust in your company’s security practices, safeguards, and risk mitigation strategy.
- Achieving this certification can open doors to new markets and opportunities that might otherwise be inaccessible.
Typically, during the sales process, a client asks their solution provider to fill out an IT Risk assessment questionnaire, sometimes called Standardized Information Gathering (SIG) questionnaire that is prepared by the client’s InfoSec, legal, compliance, and/or engineering team(s). In these instances, having an up-to-date SOC 2 audit report can greatly expedite the process of responding to these questionnaires, while also instilling confidence in the client that there is a mature information security program in place protecting their business’s data, privacy, and reputation should they choose to do business with that service provider.
Image: SOC Badge

Source: SOC for Service Organizations
As the demand for cloud-based solutions increases, SOC 2 attestation continues to be seen as the industry standard, setting apart SaaS solutions with SOC 2 audits completed from companies that do not.
Scoping SOC 2 Requirements
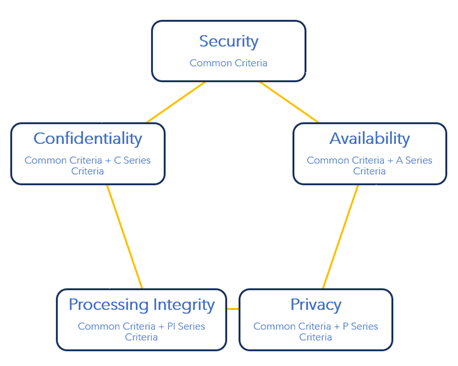
SOC 2 audits evaluate an organization’s system and organization controls based on the Trust Services Criteria, developed by the Assurance Services Executive Committee (ASEC) of the AICPA in 2017. These criteria are classified into the following five categories:
- Security
- Confidentiality
- Availability
- Processing integrity
- Privacy
The mandatory Trust Services Criteria (TSC) is Security. The Security criteria, also referred to as the Common Criteria, are required for every SOC 2 report. The other four Trust Service Criteria—Availability, Processing Integrity, Confidentiality, and Privacy—are optional and can be included based on the specific needs and objectives of the service organization and its clients.
Image: Trust Services Criteria
Source: Trust Services Critera
Of the five Trust Services categories, Security is the baseline criteria derived directly from the COSO (Committee of Sponsoring Organizations) framework, applicable to any industry. Supplemental criteria categories may be selected for a SOC 2 engagement based on applicability to your industry and the services your organization provides (view the entire Trust Services Criteria and related points of focus at AICPA).
Evaluating SOC 2 Security Controls
Security refers to the protection of:
- Information during its collection, creation, use, processing, transmission, and storage.
- Systems that store, process, or transmit data relevant to the services provided by the organization.
The following are the Security Common Criteria and their corresponding COSO principles.
CC1: Control Environment (COSO Principles 1-5)
Covers the service organization’s commitment to integrity and ethical values, independence by the board, management and board oversight, and the hiring, maintaining, and ongoing monitoring of quality employees at the service organization. It includes principles related to the commitment to integrity and ethical values (CC1), oversight responsibility (CC2), organizational structure (CC3), and human resource policies and practices (CC5).
CC2: Communication and Information (COSO Principles 13-15)
Includes the communication of relevant information to internal personnel, as well as clients of the service organization.
CC3: Risk Assessment (COSO Principles 6-9)
Meant to demonstrate the service organization is assessing risks possibly impacting their operations and putting plans in place to mitigate these risks. Risk assessments can be performed internally or by external parties for an alternative perspective on an organization’s risk posture. Good risk assessments might also include a gap analysis and provide recommendations to reduce risk.
CC4: Monitoring of Controls (COSO Principles 16-17)
Covers the ongoing evaluation of the system at the service organization and the notification to relevant personnel in the event that there is a breakdown in the system.
CC5: Control Activities (COSO Principles 10-12)
Tests the level to which service organizations have controls in place for the mitigation of risk, and certifies the controls in place are monitored on an ongoing basis. They include activities like approvals, authorizations, verifications, reconciliations, and reviews of operating performance.
The control activities (CC5) are further broken out into logical and physical access controls (CC6), system operations (CC7), change management (CC8), and risk mitigation (CC9) as detailed below:
CC6: Logical and Physical Access Controls
These controls are designed to protect the organization’s information systems and physical assets from unauthorized access.
CC7: System Operations
System operations refer to the procedures and activities involved in managing and maintaining the organization’s information systems.
CC8: Change Management
Change management involves the processes and controls for managing changes to IT systems and applications.
CC9: Risk Mitigation
Risk mitigation involves developing strategies and actions to reduce the impact and likelihood of identified risks.
SOC 2 Compliance Checklist: 4 Steps for Preparing for an Audit
We break down the four main steps to prepare for a SOC 2 audit: scoping, performing a self-assessment, closing gaps, and performing a final readiness assessment. For a deeper dive into understanding and executing a SOC 2 program, check out our SOC 2 Framework Guide: The Complete Introduction.
Step 1: Scoping
In addition to the Trust Services Criteria, other scoping considerations are your in-scope systems and any supporting systems that are involved in the execution of scoped controls. For example, your in-scope system might be the custom payroll application that you provide as a SaaS solution to various customers. To support change management, your organization might track change requests, testing, and approval through a ticketing system (like Jira or ClickUp). The outputs from your ticketing system would still be important components of the SOC 2 audit process, so it’s important to clear up scoping with your third-party audit firm before kicking off.
At this point, the SOC 2 project team, management, and leadership should understand what Type of SOC 2 report they are pursuing. There are two Types of SOC 2 reports, which go in fairly sequential and logical order. A SOC 2 Type 1 report involves a compliance audit that looks at the “design” of controls only – that is, evidence collection would involve policies, procedures, and limited samples of one to give auditors reasonable assurance that an organization’s controls are designed effectively at a specific point in time. Following the Type 1 is the Type 2, a much more rigorous compliance audit that requires the in-depth testing of control executions to determine whether the controls implemented are operating effectively over a specified period. In this latter audit, you will need to be relatively comfortable that your controls are working the right way every time.
If applicable to your business, other security frameworks (pertaining to your industry and regulatory requirements) may be added to your SOC 2 compliance program. Some of these frameworks include: HITRUST, HIPAA, ISO 27001, NIST CSF, and COBIT.
Step 2: Performing a Self-Assessment
A typical SOC 2 readiness project includes readiness activities that are carried out over several months. A part-time coordinator or security consultant may be sufficient rather than hiring an audit firm to perform the readiness assessment, especially if leveraging an effective connected risk platform to streamline SOC 2 compliance. By self-assessing against the SOC 2 criteria, organizations can identify and remediate gaps, saving them from potentially adverse findings. This will also enhance your organization’s overall security and operational effectiveness by aligning with SOC 2 best practices.
Step 3: Closing Gaps
Any findings from your self-assessment will result in the control gaps needing to be refined and closed prior to the actual SOC 2 audit. The gap remediation process generally entails:
- Develop, approve, communicate, and publish missing policies and procedures.
- Modify process workflows with gaps to protect sensitive information and manage risks appropriately.
- Conduct training sessions to ensure that all relevant staff understand the new or updated controls and their roles in maintaining compliance.
- Implement, improve, and/or optimize critical security measures and security controls, like change management, access controls, and control automation.
- Remove or terminate unauthorized access.
Step 4: Performing Readiness Assessment/Audit
Following the gap remediation process, a final readiness assessment should be conducted, where security controls are re-assessed, tested, and verified to be working as intended. This is also an opportunity to identify any effectiveness issues and to perform final remediation. This is the final step before a formal, third-party compliance audit by a CPA firm, so take this opportunity to cross your “t’s” and dot your “i’s,” especially if it’s your first time partaking in a SOC 2 audit.
Best Practices for a Successful SOC 2 Audit
SOC 2 attestations should occur on an annual basis, as reports typically cover a 3- to 12–month observation period (often with a bridge letter providing gap coverage). Thus, creating a sustainable foundation for your compliance program is key to maintaining your SOC 2 certification in the long term. Whether your organization’s SOC 2 efforts reside with your IT Audit, InfoSec, Risk Management, or Compliance function(s), developing a successful compliance program requires support across the business. Below are best practices for preparing for your SOC 2 audit:
- Assign a leader (preferably skilled with security compliance) to drive SOC 2 readiness initiatives in the organization.
- Involve stakeholders, including executive management and other leaders in the business to drive results and garner buy-in.
- Understand your weaknesses and risks, and report on any data breaches that have occurred during your audit period.
- Cultivate a clear understanding of where customer data resides and how it is protected.
- Leverage a compliance management solution to drive workflows, manage your audit checklist, and take control of the audit.
Leveraging a Connected Risk Solution to Streamline SOC 2 Evidence Collection and Attestation
As mentioned, you can save resource hours and costs when performing a SOC 2 assessment by employing a cloud-based connected risk platform. Moreover, managing your compliance program in a solution fitting your organization’s needs can be a cost-effective and efficient way to streamline your path to an unqualified opinion, while simultaneously reducing the challenges and risks of managing SOC 2 using spreadsheets, email, and shared drives. A purpose-built solution can enable you to:
- Easily scope your SOC 2 requirements.
- Centralize your SOC 2 compliance data in an environment so it can serve as the single source of truth and will allow you to see across all your controls to know which requirements they map to.
- Help you efficiently prepare for your SOC 2 audit while serving as an evidence repository and a history log of your compliance activities.
- Bring all stakeholders (Management, IT, DevOps/Engineering, Legal/HR, Physical Security) together in one place to collaborate and communicate during the SOC 2 assessment process.
- Efficiently perform assessments and facilitate formal audit preparedness through automated readiness assessment surveys.
- Streamline issue remediation and close gaps with automated workflows and notifications to issue stakeholders.
- Drive the actual audit process by enabling third-party auditors to work in a centralized platform containing all relevant data.
- Save significant resource hours and costs.
Consolidate SOC 2 and Other Audits through Integrated Risk Management Software
In addition to these efficiencies, managing your SOC 2 program with technology enables your business to easily update requirements and adopt additional compliance frameworks, without losing centralization or impacting existing testing schedules. As your compliance program grows and matures, a solution empowers your business to streamline its compliance activities across multiple frameworks to reduce repetitive administrative tasks.
Ultimately, proper preparation for obtaining your SOC 2 certification is critical, and your compliance environment is the key to your success. To learn how AuditBoard’s integrated compliance management solution can help you prepare for your SOC 2 certification and streamline your compliance program, contact us for a personalized product walkthrough today.
Frequently Asked Questions About SOC 2 Compliance
What are the benefits of a SOC 2 report?
In particular, service organizations benefit from the following advantages of having a SOC 2 report:
- Peace of mind that your security controls are designed and operating effectively over a period of time.
- Ability to efficiently and effectively respond to IT, data security, and due diligence questionnaires from customers and partners.
- Ability to provide assurance to clients and partners that your business meets their standards, expectations, and their compliance requirements.
- Helps win more customers, boost sales, and gain an advantage over competition by creating trust in your company’s security practices, safeguards, and risk mitigation strategy.
What are the five categories of the ASEC’s Trust Services Criteria?
SOC 2 audits evaluate an organization’s system and organization controls based on the Trust Services Criteria, developed by the Assurance Services Executive Committee (ASEC) of the AICPA in 2017. These criteria are classified into the following five categories:
- Security
- Confidentiality
- Availability
- Processing integrity
- Privacy
What are the 4 Steps for Preparing for an Audit with SOC 2?
We break down the four main steps to prepare for a SOC 2 audit: scoping, performing a self-assessment, closing gaps, and performing a final readiness assessment.
About the authors

Tony Luciani is a Strategic Account Executive, EMEA at AuditBoard. Prior to AuditBoard, Tony served as IT Risk and Compliance Lead at Sony Pictures. As a former InfoSec consultant, PCI QSA, and HITRUST Assessor, his experience ranges from performing gap/attestation assessments (i.e. NIST, ISO, CIS, SOC2, PCI, HITRUST, etc.) to facilitating IT risk management programs for customers across multiple industries. Connect with Tony on LinkedIn.
You may also like to read


AI usage policy: Defining acceptable AI use by employees

How Navan built a connected risk strategy with AuditBoard AI

GRC survival guide: Thriving in the era of AI SaaS

AI usage policy: Defining acceptable AI use by employees

How Navan built a connected risk strategy with AuditBoard AI
Discover why industry leaders choose AuditBoard
SCHEDULE A DEMO



